Data breaches only happen to other companies — that’s true right up until the minute your company, believing itself secure, gets hacked and finds that the personal data of millions of its customers has been exposed. A company’s reputation and competitive advantage — which may have taken decades to build — can be destroyed overnight.
For an emerging technology company, a security breach could interrupt momentum, progress and innovation. Customers and vendors have to be notified. The company’s intellectual property could be compromised, and there might be additional costs related to upgrading security and repairing operational disruptions. Internal teams need to be redirected to incident response instead of focusing on growth and progress. And if the company’s goal is to go public, a security breach might mean changes to the initial public offering filing or a disclosure to possible investors about higher capital expenditures needed to prevent future breaches. Protiviti recently published a blog post that details the challenges associated with heightened scrutiny of security in public company transitions.
A Cloud Security Mindset
It isn’t surprising, then, that in Executive Perspectives on Top Risks for 2019, a study from Protiviti and North Carolina State University’s ERM Initiative, executives in the technology, media and telecommunications industry identified the need for dedicating significant resources for privacy and network security among the top three risks.
Companies can proactively prevent breaches if a well-thought-out security plan is put in place. That’s particularly true with many of the challenges associated with the rapid pace of development in the cloud. However, cloud security cannot be treated the same as on-premises security, and companies often have trouble adjusting to the differences and shedding old mindsets and mentalities. By thinking in creative ways, IT teams can adjust to the differences, including the new challenge of sharing data with cloud providers and vendors.
Managing Security in the Public Cloud — The Shared Responsibility Model
Companies often turn to providers like Amazon Web Services, Microsoft Azure or Google Cloud Platform for their cloud transformations. But with another party involved, a question arises: Who is responsible for security?
When data storage was held on the premises, a company knew it was responsible for all of the security and infrastructure. That responsibility changes with a cloud provider. The provider and the company each carry part of the risk in what’s termed the shared responsibility model.
Most of the major cloud storage providers have published well-documented shared responsibility models online. The Amazon Web Services shared responsibility model, for example, states that Amazon’s job is to protect the cloud infrastructure, including hardware, software, networking and the facilities that run its cloud services. However, the customer’s responsibilities change depending on which Amazon services they choose to use.
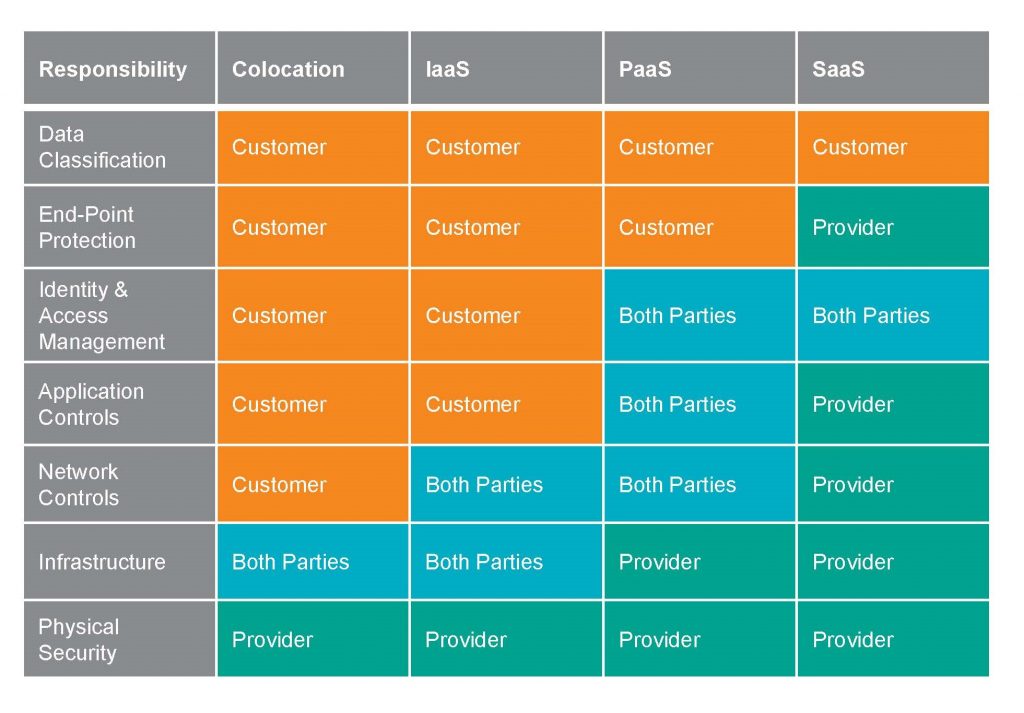
Depending on the service model — software as a service (SaaS), platform as a service (PaaS) or infrastructure as a service (IaaS) — companies need to be aware of various characteristics and benefits. For example, on SaaS applications, customers aren’t responsible for patching, data centers, operating systems or other fundamentals of running an application. However, the parameters change. The table below displays a broad generalization that illustrates where responsibilities lie for security in the shared responsibility model:
Vendor Risk Management
Public cloud providers aren’t the only organizations connecting to company data. A company’s vendors become so much a part of an organization’s daily operations that they often share network connectivity. While the HVAC or copier vendor is physically on the premises, vendors such as application suppliers and insurance companies may have access to company data via the cloud, and vendor security should be regularly reviewed and addressed.
Again, questions arise: Who owns and protects the data? What company data do vendors have access to that might be compromised? Does the vendor have access to customer records or employee information? Do they have access to financial records or marketing campaigns? These questions must be answered and addressed for every vendor the company interacts with in the cloud.
Companies can internally handle vendor risk if they have enough staff and that staff is trained in the right risk strategies. This is an investment well worth making. Some also turn to third-party benchmarking firms to facilitate these efforts. Once the right resources have been identified, it will be important to review carefully all vendor access points. Companies also should look at technical metrics to see how the data is being accessed, and they might examine the vendor’s past performance to determine whether breaches have occurred previously. If a company becomes aware of vendor risk, they can enforce more restrictive security controls around the vendor as necessary.
The Cloud Security Plan
As with vendor risk management, a successful cloud security strategy should include providing employees with cloud security training. Outsourcing for any additional specialized expertise is often part of the security plan. Knowledgeable internal personnel and expert outside consultants can confidently institute customized security plans from the onset of the cloud transition.
The security plan should be centralized so that all parts of the organization can be monitored from one place. Approval for the security plan should come from all levels of management, and the plan should be regularly monitored. These shouldn’t be one-size-fits-all security plans. Cloud software is flexible, so companies can design and refine their security plans to meet their own business needs. Organizations should look carefully at their business goals and create a security plan that protects data while enhancing related security processes.
No company can guarantee that it won’t become the victim of a data security breach, but having a carefully executed cloud security plan will enable it to go a long way toward protecting its data — and reputation.






