Technology, media and telecommunications (TMT) company leaders are under growing pressure to identify and remediate potential gaps in policies and processes — especially those related to data privacy and cyber supply chain networks — that could expose their organizations to regulatory risks. During a recent webinar with audit professionals, Protiviti subject-matter experts discussed the growing concerns around cyber supply chain and data privacy, and what organizations can do to mitigate these issues. Below is a summary of the key takeaways from the event.
Data privacy: implementing controls and monitoring effectiveness
A major push to pass a new federal privacy legislation, the American Data Privacy and Protection Act (ADPPA), is just one facet of the intensifying regulatory landscape for TMT businesses.
A few top-of-mind data privacy issues
- The U.S. Federal Trade Commission’s pending lawsuit against a data broker over the company’s alleged sale of geolocation data that could be used to trace individuals in locations such as health clinics is one example of the agency’s heightened interest in data privacy matters. This case is being followed closely across the industry.
- States like Utah and Virginia plan to pass new data privacy legislation in 2023, and others like California, Connecticut and Colorado are stepping up enforcement of existing data privacy laws. California’s attorney general, for example, is fining companies for selling consumer data without proper disclosure or providing the ability for consumers to opt out of that process.
- The stringent new Trans-Atlantic Data Privacy (TADP) framework, which the United States and the European Union (EU) agreed to earlier this year, addresses data privacy and protection of EU citizens’ data and replaces previous agreements like the Safe Harbor Framework and Privacy Shield Framework, which EU courts had overturned.
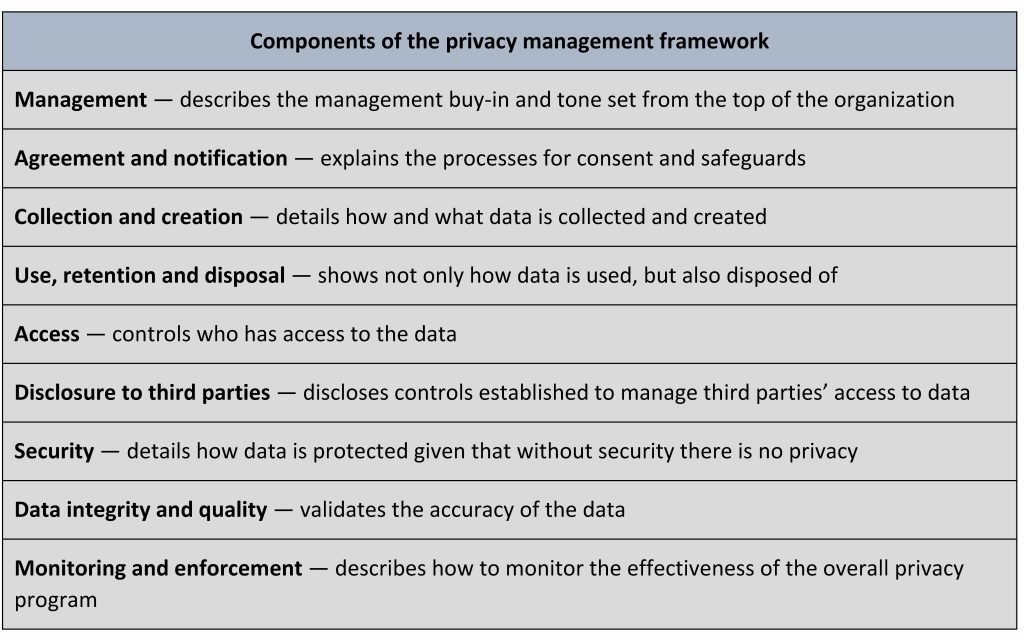
TMT companies can take a more proactive stance toward creating a comprehensive data privacy program, or privacy by design, using this Privacy Management Framework (PMF), which addresses the following key components:
Typically, when TMT companies set out to build a data privacy program or are trying to mature their existing program, they struggle in these two areas: privacy by design and continuous monitoring.
Privacy by design
This is a proactive process for ensuring that, as technology products change — which they do, frequently — privacy remains a visible requirement for end users. That means privacy must be built into both new and current products. For example, when a user turns on a new application, privacy is the enabled option, and it’s the user’s decision to allow a less secure and less privacy-oriented setting.
Embedding privacy into a product design requires bringing the appropriate expertise into the development process from the start — meaning, having privacy engineers sitting at the table with functional engineers to define the requirements for the product’s privacy features. Data mapping and classification are foundational to privacy by design and should be included as part of the security development lifecycle.
Continuous monitoring of privacy controls
Privacy controls can stop operating as intended for various reasons, from technology changes to human errors. Often, when those controls stop working, nobody notices — until there’s an issue. Continuous monitoring can help companies stay on top of potential problems with privacy controls. This process, which involves the periodic generation and review of reports by the organization’s first or second line of defense, can help companies surface and remediate potential issues more quickly than periodic controls testing.
Cyber supply chain: assessing current vulnerabilities
The other critical area of focus discussed during the webinar was cyber supply chain. According to recent data from the European Union Agency for Cybersecurity (ENISA), out of 24 supply chain attacks reported in the period from January 2020 through early July 2021, eight (33%) were reported in 2020 and 16 (66%) were reported from January 2021 to early July 2021. This attack vector is poised to grow exponentially over the next few years.
Sabotage and the theft of information, including intellectual property, to gain an economic or a military advantage, are the primary motivations for threat actors responsible for cyber supply chain attacks. TMT companies can fight back by taking a comprehensive approach to securing their cyber supply chain, including implementing a cyber supply chain risk management (C-SCRM) policy and a formal program to support it. That includes identifying all the various stakeholders responsible for cyber supply chain security, including engineering, finance and procurement staff, appointing a C-SCRM senior risk officer, and integrating C-SCRM considerations into enterprise risk management efforts.
Addressing cyber supply chain risks
Addressing cyber supply chain risk involves a level of complexity that goes beyond traditional risk management. To achieve that future state, TMT companies should first determine how vulnerable they are now to these types of attacks, which range from hackers compromising software development tools or infrastructure, to embedding malicious code in the firmware of components to gain access to a system or network, to preinstalling malware on devices, including USB drives and cameras. Conducting a third-party risk assessment is a must to determine that these vendors also have appropriate supply chain risk management policies and programs in place, as they are often key targets for attackers who use them as stepping stones to reach bigger and more valuable targets.
To learn more about data privacy and cyber supply chain risks impacting the TMT industry, and the steps companies can take to manage these risks appropriately, watch Protiviti’s webinar, “Tech, Media & Telecom: Top Risks — Where Are We Now and What’s to Come?” View it on-demand here.
Protiviti Managing Director Christine Halvorsen contributed to this article.