Cyber attacks continue to rank among the leading business concerns in 2020, according to the eighth annual Executive Perspectives on Top Risks, a joint survey by Protiviti and NC State University’s ERM Initiative. Drawing on responses from 1,063 board members and executives from around the world, the survey found that cyber threats represented a “significant impact risk” to senior managers, one that could disrupt core operations and damage an organization’s brand.
To take a closer look at cybersecurity, Protiviti joined ESI ThoughtLab and a group of other prominent organizations to launch The Cybersecurity Imperative. The aim of the project was to tap the best minds in the industry to assess the impact of cyber intrusions and develop benchmark approaches. Although the study paints a broad picture of a proliferating criminal front, it also offers specific recommendations to bolster cybersecurity. Below, I summarize the top trends, and actions boards can take to prepare.
What to Expect in 2020: Top Trends
The pace and scope of cyber threats is evident in how quickly criminals are adapting to changes in security practices. Among the top trends in 2020 are the following:
Biometric Attacks. “Unique human identities” in the forms of fingerprints, voice and face ID are becoming more popular in consumer devices, but they also are attracting cyber attackers who seek access to comprehensive biometric data by breaking into these profiles. A stolen biometric password is “the gift that keeps on giving” as it is not likely to ever change.
Social Media Alerts. Facebook and other social platforms increasingly play a part of governmental infrastructure as a way to disseminate information and promote awareness or engagement. However, social media can also lead to false alerts with potentially catastrophic results, such as the bogus missile attacks reported in Hawaii and Japan, as we recently experienced.
Commercial Espionage. Such espionage is an ongoing threat, but nations on the losing side of a trade war may well be incentivized to enhance their efforts to steal intellectual property, using ever more sophisticated techniques.
Supply Chain Vulnerability. Already, some nations are targeting the supply chain at the chip level to gain backdoor access.
Zero Trust. This is not a threat but an approach more security teams are adopting to stop lateral movement once an attacker has gained entry. It involves micro-segmentation and granular access control, trusting nothing and no one inside the system.
The challenge in protecting all of these fronts is that data runs our entire society from server to served. It must be accessible anytime and anywhere, that is, with a multitude of constantly open access points. Moreover, a recent study indicated that chief information security officers can monitor, on average, only 67% of an enterprise. That leaves a lot of exposure.
Prioritization: Ranking of Vulnerabilities
One of the key findings of the Cybersecurity Imperative is the ranking of the greatest vulnerabilities of IT systems, shown here:
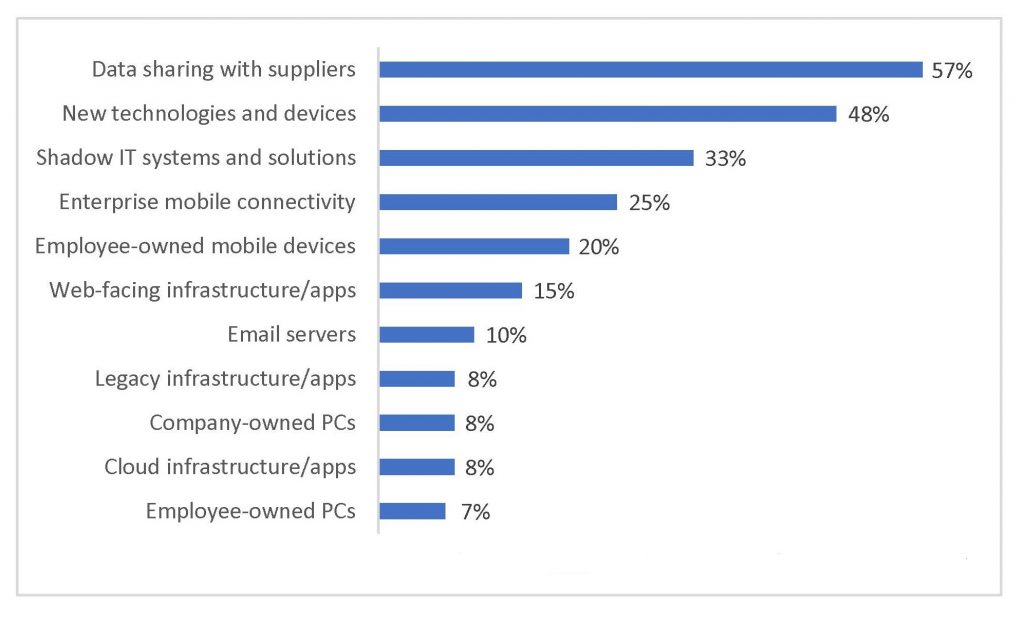
As the chart illustrates, 57% of respondents report data sharing with suppliers as the weakest point of an organization’s defenses. Generally, most firms can be assured of a safe data exchange with their major suppliers. But imagine a small vendor becomes the victim of a hired hacker. For as little as $300 in the current criminal market, an intruder can be hired to try to break the vendor’s security and gain access to an organization’s IT system.
The most common form of intrusion, according to the survey, is malware, which is introduced usually through phishing. Not only is phishing inexpensive, but it can also bypass the most extensive security protections. All it has to do is prey on the judgment of individual employees by tailoring its lure as a legitimate need. Once inside a system, an attacker can introduce viruses, malicious apps and ransomware, and next attempt to move laterally to compromise other systems.
Recommendations to Bolster Security
Boards and senior management can take a number of actions, ask probing questions and generally set the tone to make cybersecurity a priority. Among them:
- Balance protective efforts with recovery capabilities. A breach will happen; what matters is how quickly an organization can rebound. Attack drills would greatly benefit a firm’s ability to respond to the inevitable intrusions.
- Don’t be overly confident. Surprisingly to some, digitally advanced organizations report more attacks than “beginner” firms. The lesson here is that digital security must be part of the digital transformation process, even for “born digital” firms.
- Embed risk and cybersecurity into the work of innovation teams. The last thing an organization wants is cybersecurity competing as a separate item for scarce budget dollars against innovation.
- Maintain ongoing training programs for the staff, and continue to assess insider risk.
- Set risk appetite thresholds using a quantitative risk analysis, such as the Factor of Analysis of Information Risk (FAIR) methodology. Cybersecurity might seem expensive, but it could be a bargain compared to the exorbitant costs of exposing critical data.
- Take constant stock of the ever-changing threat landscape. No longer are financial firms the prime targets. Now that ransomware has become a moneymaking activity, any organization is potential prey for loss of data or functionality.
- Take an active interest in cybersecurity. Ask probing questions, set clear expectations and monitor focused dashboards. Publics are now rating board performance on cybersecurity, as well as more traditional areas, such as safety and financial return.
Baking In Security
Cybersecurity is a challenging proposition, but it is part and parcel of doing business in the 21st century. Consequently, organizations that bake in cybersecurity as part of their growth DNA will be more prepared to maintain their systems and recover from attacks. These capabilities also become a component of an organization’s competitive edge.
Read additional posts on The Protiviti View related to cybersecurity.





